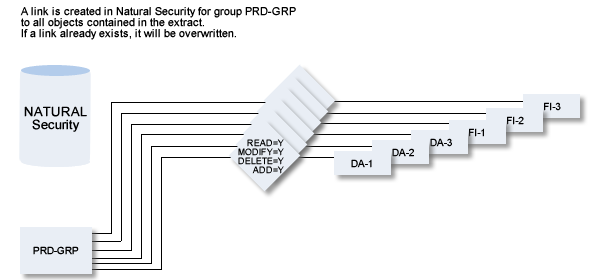
With the special function Mass Grant in NSC you can create security definitions in Natural Security for all Predict objects contained in an Extract.
See the Predict Security documentation for more information.
This section covers the following topics:
The following prerequisites must be met before you can use this function:
Natural Security must be installed.
Default values for the Natural Security file must be specified under Defaults > General Defaults > Protection > DBnr/Fnr of NSC file. For this function, the current Natural Security file must be the same as the Natural Security file used when starting the Natural session.
Default definitions must already have been added in Natural Security with the special function Maintain NSC Definitions > Add NSC Default Definitions. See Add NSC Default Definitions - Code A.
An Extract containing all objects to which the user or user group is to have access must exist. See the section Extract in the Predefined Object Types in Predict documentation.
If you wish to grant access to a user or group, this user or group must already be defined in Natural Security.
This function only makes sense if you create an Extract using a Restriction such as Owner or Keyword.
If you wish to protect a range of Predict objects (for example, all Files that start with ABC), it is better to create a corresponding definition in Natural Security using asterisk notation.
In earlier Predict versions, information such as Keywords or Owners was evaluated to restrict access to objects. Many customers used this method to adapt their environment to the particular security requirements of their company.
Predict Security gives you a whole range of new possibilities for defining your security environment which makes most of these customer solutions obsolete. We therefore recommend the following:
Everything a user may do or may not do should be defined centrally in Natural Security.
Create an Extract and enter as Restrictions the keyword or owner information, for example, that you evaluated in earlier versions of Predict.
Execute the function Mass Grant in NSC for this extract.
For more information see the Predict Security documentation.
The Mass Grant screen is called with code M in the Special
Functions menu or with the command SPECIAL MASS.
10:58:04 ***** P R E D I C T ***** 2017-05-31
Plan 7 - Mass Grant in NSC -
Extract-ID ...................*
Action .......................* T
Definitions in NSC Read Add Modify Delete
Default ....................... * * * * (Y,N,*)
NSC User/NSC Group ... (Y,N,*)
Command ===>
Enter-PF1---PF2---PF3---PF4---PF5---PF6---PF7---PF8---PF9---PF10--PF11--PF12---
Help Next Stop Last LnkEl Flip Print Impl AdmFi SelFi Prof Main |
| Parameters | |||
|---|---|---|---|
| Extract ID | ID of the extract containing the objects for which a security profile is to be maintained. | ||
| Action | S | Save. NSC definitions are added as specified for the objects contained in the extract. | |
| T | Test. NSC definitions are listed for the objects contained in the specified extract, but no data is written to Natural Security. | ||
| Default | Each security object in Natural Security has a default definition. Permission is added as defined in this screen if no definition already exists. Existing security definitions are not overwritten. Possible values: | ||
| Y | Access is granted for the respective access mode. | ||
| N | Access is denied for the respective access mode. | ||
| * | Inherit. The security definition of the higher level object is taken if appropriate. | ||
| NSC User/NSC Group |
Enter the ID of the user or group for which you wish to create a security definition. The user/group must already exist in Natural Security. A link is created between the user/group and the objects contained in the extract. If a link already exists, it will be overwritten. |
||
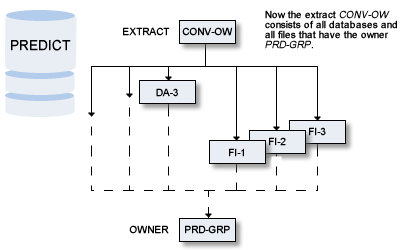
In an earlier version of Predict, only users of the group PRD-GRP were allowed to access Files and Databases in Predict. Access to these objects was controlled by evaluating Owner information with a User Exit. Now Administrator ADMIN-1 wants to add this information as security definitions in Natural Security.
There are various methods of creating an extract containing all files and databases with the owner PRD-GRP. The methods available depend on the editor you are using and are described in detail in the section Extract in the Predefined Object Types in Predict documentation.
You must execute two Retrieval functions: one for files, the other for databases. The screen below shows the function Build / extend an extract for object type DA.
Enter code D for Retrieval type and code L for Output mode without specifying any other search criteria. Enter T in the field Restrictions for a temporary profile, and enter PRD-GRP in the field AND with owner. See below.
13:59:03 ***** P R E D I C T ***** 2007-05-31
Plan 10 - Build/exte +Top------------Restriction---------------
! With keyword(s) !
Extract ID ......... CONV-OW ! !
! !
! !
Build extract for object type ..* DA ! !
! !
Retrieval type .....* D ! combined by (AND/OR) OR !
Output mode ........* L Select ! AND with owner !
!
PRD-GRP
!
Search criteria ! BUT NOT with keyword !
Database ID ....... ! !
In Virtual machine ! AND included in extract !
! !
! AND containing the string !
! !
Drop existing objects N (Y,N) ! Scan options: !
List objects ........ Y (Y,N) ! Abstract N (Y,N) Rules ..... N (Y,N) !
! Descr. N (Y,N) Object ID . N (Y,N) !
Restrictions .......* T Profile HNO ! Absolute N (Y,N) Ignore case N (Y,N) !
Output options .....* Profile HNO !Command ==> +___ !
+More-------------------------------------
|
This function will add all databases with the owner PRD-GRP to the extract CONV-OW.
Perform another retrieval operation for object type file with the same temporary profile.
Call the special function Mass Grant in NSC with Code M in the Special Function Menu. Enter the values as shown in the screen below:
13:43:44 ***** P R E D I C T ***** 2007-05-31
Plan 7 - Mass Grant in NSC -
Extract ID ...................* CONV-OW
Action .......................* S
Definitions in NSC Read Add Modify Delete
Default ....................... n n n n (Y,N,*)
NSC User/NSC Group prd-grp ... y y y y (Y,N,*)
|