Host/Client Security
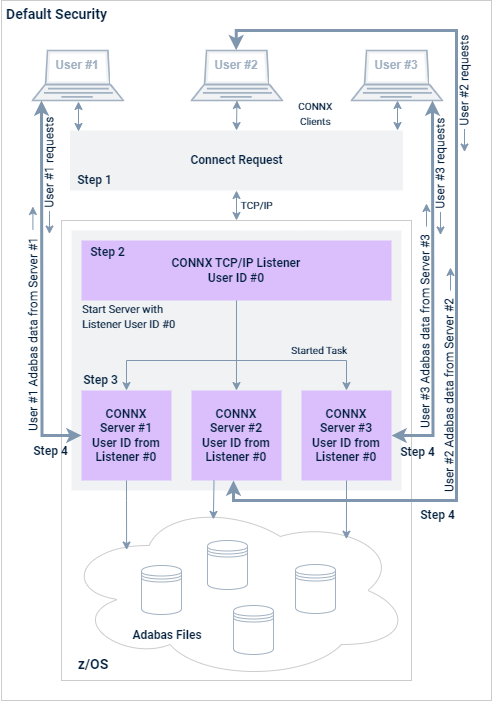
Adabas SQL Gateway is implemented as a Windows PC client and a pair of z/OS programs: the Listener (CNXRUNA) and the Server (CNXRUNB). An Adabas SQL Gateway user connects from a client application through a supported interface (ODBC, JDBC, OLE DB, or .NET) to the CONNX TCP/IP Listener program, which starts the Server program in the Listener's batch address space. Refer to steps 1 through 3 in the following figure. Once started, the Server sets up a separate TCP/IP connection to the invoking CONNX PC client.
Default Option
The host-side security logic for user ID and password verification can be enabled or disabled for CONNX client-server connections via a CONNX environment variable. Setting CNXNOPREAUTHORIZE to a non-zero value instructs the Adabas SQL Gateway TCP/IP Listener and Server programs to bypass user ID and password verification. Once the Listener program starts a Server program, client requests and data flow from the CONNX PC client to the server and back via a dedicated TCP/IP socket connection.
This security option bypasses the need to execute the CONNX programs from an APF-authorized load library. An advantage to this approach is that user ID and password security rules for CONNX PC clients need only be defined for each z/OS user ID which starts the Server.
Alternate Option
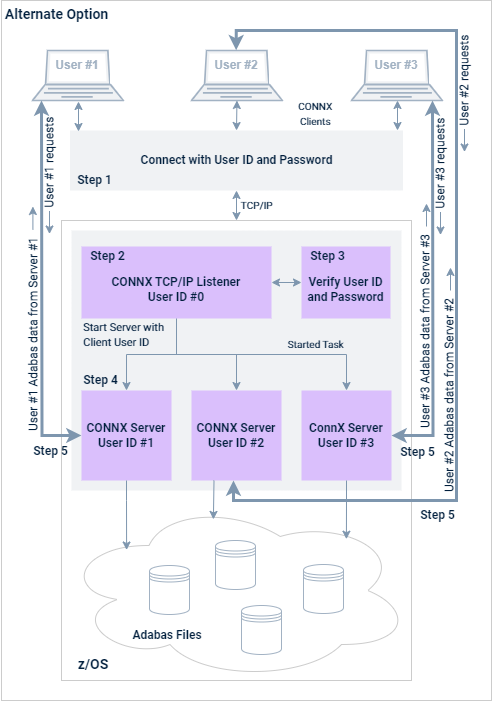
Setting CNXNOPREAUTHORIZE to zero instructs the Adabas SQL Gateway TCP/IP Listener and Server programs to execute the host-side user ID and password verification logic. The CONNX PC client component sends an encrypted user ID/password pair to the CONNX TCP/IP Listener program, which decrypts the user ID and password and executes the RACF (Resource Access Control Facility) VERIFY macro. If the user ID/password pair is valid, the Server program starts the Listener program in the Server's batch address space. Refer to steps 1 through 3 in the following figure. Once started, the Server program sets up a separate TCP/IP connection to the invoking CONNX PC client. Client requests and Adabas data responses flow back and forth directly from the CONNX PC client to the dedicated CONNX Server. Refer to steps 4 and 5 in the following figure.
The alternate security option observes the host-side security rules defined for user ID and password verification. In order for these rules to be enforced, the Listener and Server programs must run from an APF (Authorized Program Facility) load library. The operator command (SETPROG APF) necessary to add the Adabas SQL Gateway load library to the APF list is documented in
Verifying the Installation and Starting the CONNX Listener.
CONNX Client-Side Security and Host-Side Security
For both options, the CONNX Administrator should consider taking advantage of the client-side security features implemented in the CONNX Data Dictionary (CDD). The first line of defense is only to import selected Adabas files into the CDD. Additionally, the CONNX Administrator can restrict file access based on CONNX user IDs and groups defined via the security menu features in the CONNX Data Dictionary Manager.
In some cases, a physical Adabas file is composed of multiple logical files or sub-files. The CONNX Data Dictionary Manager can be used to define and enforce security rules based on these logical files, as well as on the underlying physical data sets. Further, column- and row-level security can be implemented by defining one or more CONNX views against the imported Adabas files, and by authorizing individual or groups of CONNX user IDs to execute the CONNX client-side views.
The CONNX client-side approach to security complements and enhances host-side security products, such as IBM RACF, CA-ACF2, and CA-Top Secret. In all cases, the security rules defined in the CONNX Data Dictionary take precedence over the host-side security rules. For more information on CONNX client-side security, refer to the CONNX User Reference Guide, available online, on the CONNX CD-ROM, and within the CONNX application.
Adabas SAF Security
The usage of SAF Security can be activated "after the fact"; without re-installing the data server component. The following steps are required to enable SAF Security support on z/OS:

APF-authorize the SQL Gateway load library.

Update the CONNX Listener parameters.

Edit the member
CNXPARMS.

Set
CNXNOPREAUTHORIZE to
0.

Set
CNX_PASS_TICKETS to
1.

Restart the z/OS data server.
In addition, the following actions are also recommended:

Define CDD password to restricted access to the CDD.

Disable "CONNX Integrated Security" in CDD, when user accounts are not added to the CDD.

Enable JESSPOOL-Access for all SQL Gateway users; the RACF default for JESSPOOL is (ACCESS=NONE).