This section describes network design considerations. It covers the following topics:
Network design is critical to providing the best response time to client applications. Client/server applications tend to multiply rapidly, causing networks to expand without following a carefully considered design plan. Entire Net-Work is often installed after a major local or wide area network is already in place.
Whether you are working with a new network or an existing one, it is important to make and follow a plan when installing Entire Net-Work in order to best utilize the existing facilities and provide the best possible response time to your applications.
The information in this section refers to the following Entire Net-Work components:
| node | An Entire Net-Work instance. |
| target | A source of information, such as Adabas, EntireX Communicator, or Entire System Server. |
| client | An application that is accessing a target. |
Entire Net-Work should be designed to use the same topology used by the underlying network. There are usually several underlying layers of logical and physical configurations that are invisible to Entire Net-Work. Those who design and maintain these underlying layers should be involved in the network design process.
Several topologies are discussed in this section. The bus topology is not included because it does not readily apply to Entire Net-Work configurations.
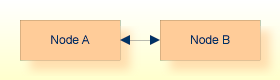
Point-to-point is the simplest of all configurations. It consists of two nodes connected by a link, and is the way most networks start; for example, a workstation client application using a direct connection to access a mainframe database.
Many modern networks run TCP/IP in a formation that logically consists of many point-to-point sessions. For example, a given client could be attached to FTP://157.189.1.1/etc/file as its server.
The following diagram illustrates the point-to-point configuration:
Point-to-point networks often evolve into Star networks. A central controlling node is attached to each node in the network. The following diagram illustrates the star configuration:
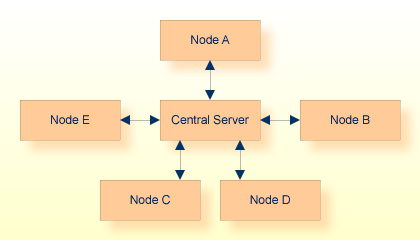
Although targets are normally run on the Central Server, a target running on any attached node is only two hops away from any potential client. The Star configuration is limited by the speed of the central processor. Its advantage is that it allows central control of the network, which facilitates problem determination.
The original IBM VTAM networks were designed as Star networks, where VTAM itself ran in the central processor and had absolute control over all attached physical and logical units.
As its name implies, nodes in a Ring network are arranged in a ring, as shown in the following diagram:
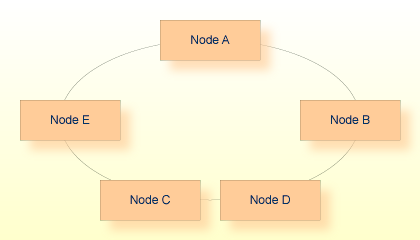
In the Ring configuration, it is not apparent which node is the server and which is the client. For this reason, the Ring network is often used among peers, such as Unix servers or mainframes, where clients or servers may run on any node. Because all nodes are peers, problem determination can sometimes be difficult. An advantage of the Ring configuration shown above is that any node is only two hops away from any other node. This configuration also provides built-in redundancy.
It is difficult to determine the best way to build your Entire Net-Work configuration. The Star configuration tends to work best in smaller networks, allowing some central control and the ability to route traffic in the most advantageous way. As the network grows, it is important to carefully consider the placement of targets within the network to keep them logically or physically closer to the clients they serve. This may requires a combination of topologies. The configuration in the following diagram, for example, contains a ring of Star networks:
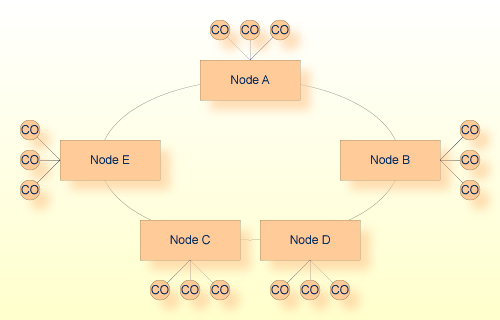
Each server node (Node A, Node B, etc.) acts as the central processor for a group of client-only (CO) nodes, and the server nodes are arranged in a ring formation. None of the client-only nodes is allowed to run a target, so no target can be more than four hops away from any client.
For purposes of this discussion, redundancy means providing multiple paths between nodes. The underlying network may already be redundant. Consult those responsible for maintaining it before implementing redundancy with Entire Net-Work. If implemented incorrectly, the higher level redundancy could defeat the underlying redundancy. Redundancy can be implemented with Entire Net-Work by running heterogeneous links in parallel or by providing multiple paths between nodes via interconnectivity.
Interconnectivity requires that a physical path exist between all points. In the following diagram, for example, traffic can pass in either direction around the ring. If the link between node C and node D is severed, traffic must pass through nodes B, A, and E to connect node D to node C.

When constructing a logical ring in order to provide redundancy, it is best to determine where the majority of the traffic exists. If most of the traffic moves between node A and node E, for example, putting node D in the middle would add unnecessary processing to the traffic pattern.
Weighting is used to prioritize connections. When two or more connections can be used to reach a target node, Entire Net-Work uses the lowest weighted connection available.
Carefully consider weighting the links in your network to provide the most efficient movement of traffic. Assign the lowest weight to the primary link. Assign higher weights to connections that are slower or more expensive; these connections may be used as backup. If the primary connection is severed, traffic can flow over the backup connection. It is important that the connections not share the same physical path.
The example network in the following diagram has both a TCP/IP connection and a VTAM connection between each pair of nodes. If traffic moves at 10 megabits per second on the TCP/IP link and 56,000 bits per second on the VTAM link, the VTAM link should be used as a backup to the TCP/IP link. Giving the TCP/IP link the lower weight ensures the most efficient flow of traffic.
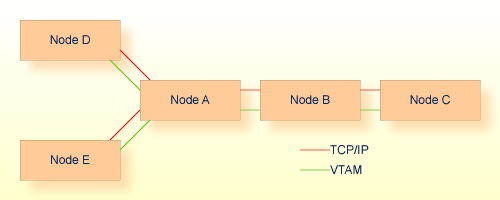
The movement of traffic is the core consideration of network design. The following considerations should be kept in mind when designing an Entire Net-Work Configuration:
Nodes that share the greatest amount of traffic should be directly connected.
The lowest weights should be assigned to the links with the highest throughput.
Maintenance traffic should be taken into account.
With the exception of client-only nodes, all nodes know about all other nodes in the network and all nodes know about all targets in the network. This is accomplished using broadcast technology.
The first time a node connects to another node in the network, the node that receives the connection sends a message to all the nodes to which it is connected informing them of the availability of the new node. If the new node has others connected to it, then this information is broadcast throughout the network. The newly connected node may also have to broadcast information regarding connected nodes at the other end.
Broadcasting also applies to targets. When a target becomes available or unavailable, the node where it resides will broadcast this information to all the nodes to which it is connected. The broadcast is passed down the line until all nodes in the network are aware of the target's status.
In a large network, broadcasting can create thousands of messages of ever increasing length just to keep every node informed of the status of all known nodes and targets. To prevent wasting CPU cycles and bandwidth on redundant or unnecessary information, it is important to keep broadcast traffic to a minimum.
There are two good ways to manage this situation:
Use client-only nodes with the client mode setting turned on.
Implement redundancy and connectivity in a way that minimizes unnecessary broadcast traffic. Consider the following ring configuration:

In the Ring configuration shown above, it may be tempting to connect node A to nodes C and D, node B to nodes C and E, and so on to provide the most redundant and direct paths possible. Rather than being helpful, however, this creates a great deal of unnecessary broadcast traffic any time a target's status changes on any given node. For example: When a target becomes available on node A, A sends a broadcast to nodes B, C, D, and E. Each of these nodes then rebroadcasts the information to its connected nodes, which in turn creates more broadcast information.
| Warning: An overly connected network creates a great deal of undesirable traffic and excessive CPU usage. For this reason, Software AG does not support interconnectivity of more than three nodes. |
Many workstation Entire Net-Work nodes are used only to run clients. Because client-only nodes never contain a running target, information about them need not be broadcast around the network.
Entire Net-Work for the workstation provides a client mode setting. Client mode tells Entire Net-Work that no information about that node is to be broadcast. If the network has 10 machines that run targets, and 1000 machines that run clients only, the use of the client mode setting clearly results in a large reduction in broadcast traffic.
A hop is defined as traffic passing from one node to the next. The point-to-point configuration shows one hop.
Entire Net-Work must manage information about how to move data between all nodes on the network.
Consider the following example:
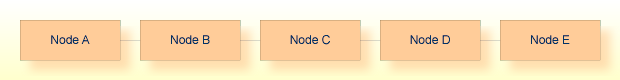
In order for node A to get to node E, node A must maintain path information that states that node E is available via node B. It must also, however, maintain path information about all other nodes in the path.
| Warning: As a path becomes longer, it becomes increasingly difficult to correctly maintain information about all nodes and paths. For this reason, Software AG does not support more than four hops. |