CONNX Supports SSL/TLS connections from the pure java JDBC Driver to the 32bit and 64bit JDBC Server service running on Windows or Unix.
In order to use CONNX with SSL when connecting with JDBC, the following requirements must be met.
Use openssl to create your certificate and key file.
CONNX ships with a 64bit OpenSSL command line. It is located in the OpenSSL directory under the root of your 64bit CONNX installation.
Open a command prompt, and navigate to this directory.
Please refer to OpenSSL documentation for details on all of the possible
settings when creating keys and certificates. Here is an example
of a self-signed key an certificate creation:
openssl req -nodes -x509 -newkey rsa:4096 -keyout key.pem -out cert.pem -days 365 -config openssl.cnf
In the above example, key.pem is the private key file, and cert.pem is the certificate file. Both of these files will be required when configuring the SSL Listener.
The certificated used in the JDBC server must be imported into the Java security store.
First, identify which Java jdk/sdk the application uses. Then, locate the "cacerts" security file under that directory structure.
Then use the keytool utility to import the certificate. The default password for a java security store is "changeit" - you will be prompted
for the password of the security store.
Here is an example of how to import a certificate into the java security store:
c:\Program Files (x86)\Java\jdk1.7.0_17>keytool -import -alias example -keystore "C:\Program Files (x86)\Java\jdk1.7.0_17\jre\lib\security\cacerts" -file c:\project\connx\OpenSSL32\server.crt
If you are not using the latest version of Java, you may be using a version that has a default policy of a limited cryptographic key length.
If you are not using one of the Java versions listed below, you will need to download and install the "Java Cryptography Extension (JCE) Unlimited Strength Jurisdiction Policy" for your version of Java.
As an example, for Java 8, it is located here: http://www.oracle.com/technetwork/java/javase/downloads/jce8-download-2133166.html
Versions of Java that have a default policy of unlimited cryptographic key length (and do not require any changes):
To Enable CONNX SSL for ESS, the following CONNX configuration setting must be set:
CONNX.JDBC.CNXLISTENSSL must be set to 1
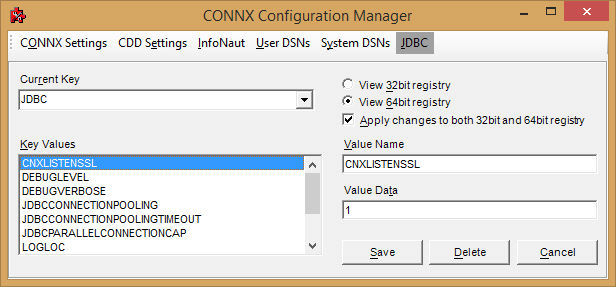
Transfer your SSL Certificate and key to system running the CONNX JDBC Servers.
Define two configuration settings that will point CONNX to the certificate and key called CONNX.JDBC.SSLCERT and CONNX.JDBC.SSLKEY.
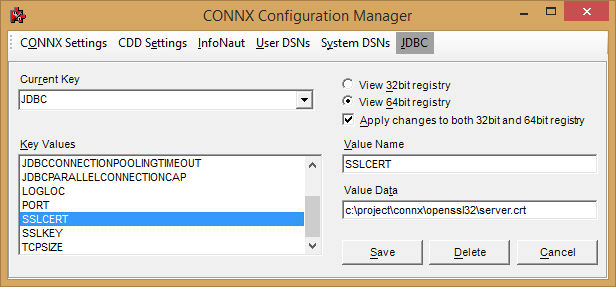
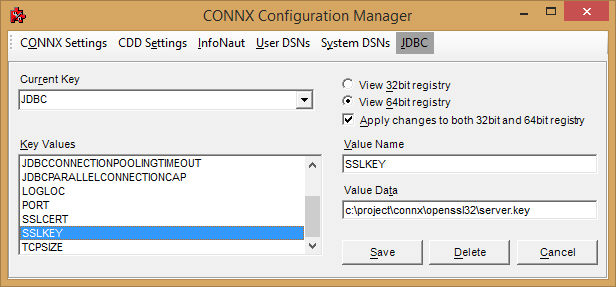
Once these setting changes are made, the JDBC server must be restarted.
On the client (the Java application), a new setting must be added to the connection string to enable SSL connections to the JDBC Server.
The setting name is SSL, and it should be set to a value of true.
Here is an example connection string with SSL enabled: jdbc:connx:DD=oracle;Gateway=localhost;Port=7500;ssl=true