MS Azure - DBaaS Use Case
The following use case takes a deeper dive into a production environment that runs Adabas Cluster on Azure as a "Trusted MS Azure Network".
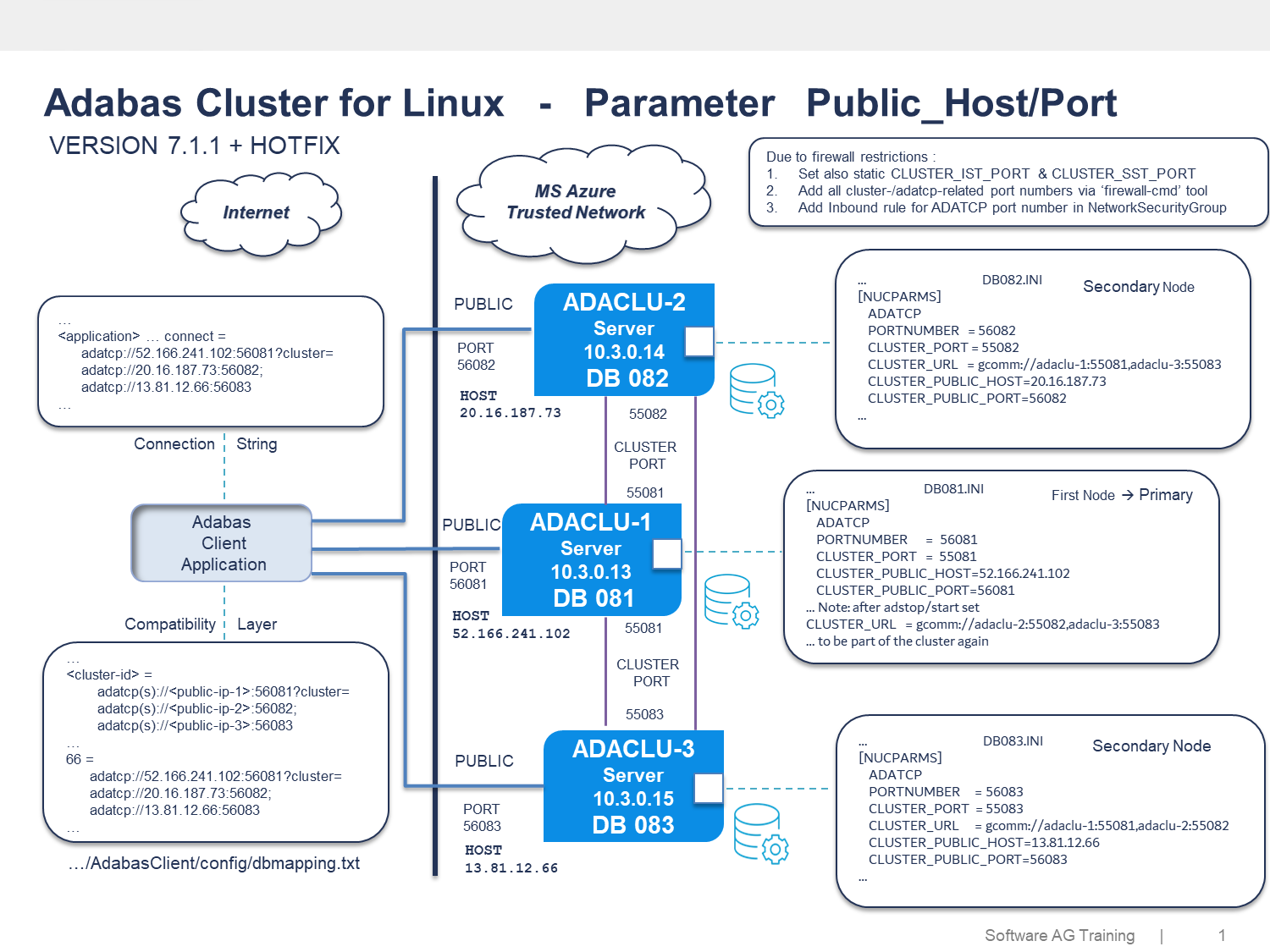
In such a scenario, a host may have two IP addresses: An internal private IP and an external public IP. Clients accessing the cluster require the nodes to share this external IP information, possibly involving an application server on the internet.
In a distributed architecture like this, and to ensure security, network segmentation is mandatory, as it is not best-practice to run all components in a single network segment. The following Database-as-a-Service example shows how to address this security requirement using the parameter CLUSTER_PUBLIC_HOST.
Architecture
The following graphic shows the configuration of a three node Adabas Cluster in a trusted MS Azure network environment as well as the Adabas Client (Application Server) located on the internet.
Step-by-step Instructions
1. Set up three nodes with Adabas version 7.1.1 or higher with the latest hotfix installed on a Linux 9 system in an MS Azure cloud environment. Configure the Azure host using a static public IP address.
A public IP address allows Internet resources to communicate inbound to Azure resources. Either use the Azure Portal to determine the public IP address, or execute the following command in the local shell environment:
[sag@ADACLU-1 ~]$ curl ifconfig.me
52.166.241.102
2. Set up your application server with Adabas Client version 7.1.1 or higher with the latest hotfix installed in an external environment.
3. Create the database on every node, e.g. crdemodb 81, and define all cluster related parameter.
ADACLU-1
...
adaini dbid=81 add topic=nucparms item=ADATCP
adaini dbid=81 add topic=nucparms item=portnumber=56081
adaini dbid=81 add topic=nucparms item=cluster_port=55081
adaini dbid=81 add topic=nucparms item=cluster_ist_port=55998
adaini dbid=81 add topic=nucparms item=cluster_sst_port=55999
adaini dbid=81 add topic=nucparms item=cluster_public_host=52.166.241.102
adaini dbid=81 add topic=nucparms item=cluster_public_port=56081
adaini dbid=81 mod topic=nucparms item=OPTIONS=AUTO_EXPAND
...
ADACLU-2
...
adaini dbid=82 add topic=nucparms item=ADATCP
adaini dbid=82 add topic=nucparms item=portnumber=56082
adaini dbid=82 add topic=nucparms item=cluster_port=55082
adaini dbid=82 add topic=nucparms item=cluster_ist_port=55998
adaini dbid=82 add topic=nucparms item=cluster_sst_port=55999
adaini dbid=82 add topic=nucparms item=cluster_url=gcomm://adaclu-1:55081,adaclu-3:55083
adaini dbid=82 add topic=nucparms item=cluster_public_host=20.16.187.73
adaini dbid=82 add topic=nucparms item=cluster_public_port=56082
adaini dbid=82 mod topic=nucparms item=OPTIONS=AUTO_EXPAND
...
ADACLU-3
...
adaini dbid=83 add topic=nucparms item=ADATCP
adaini dbid=83 add topic=nucparms item=portnumber=56083
adaini dbid=83 add topic=nucparms item=cluster_port=55083
adaini dbid=83 add topic=nucparms item=cluster_ist_port=55998
adaini dbid=83 add topic=nucparms item=cluster_sst_port=55999
adaini dbid=83 add topic=nucparms item=cluster_url=gcomm://adaclu-1:55081,adaclu-2:55082
adaini dbid=83 add topic=nucparms item=cluster_public_host=13.81.12.66
adaini dbid=83 add topic=nucparms item=cluster_public_port=56083
adaini dbid=83 mod topic=nucparms item=OPTIONS=AUTO_EXPAND
...
4. Create firewall rules for the trusted network.
ADACLU-1
sudo firewall-cmd --add-port=56081/tcp
sudo firewall-cmd --add-port=55081/tcp
sudo firewall-cmd --add-port=55081/udp
sudo firewall-cmd --add-port=55998/tcp
sudo firewall-cmd --add-port=55999/tcp
ADACLU-2
sudo firewall-cmd --add-port=56082/tcp
sudo firewall-cmd --add-port=55082/tcp
sudo firewall-cmd --add-port=55082/udp
sudo firewall-cmd --add-port=55998/tcp
sudo firewall-cmd --add-port=55999/tcp
ADACLU-3
sudo firewall-cmd --add-port=56083/tcp
sudo firewall-cmd --add-port=55083/tcp
sudo firewall-cmd --add-port=55083/udp
sudo firewall-cmd --add-port=55998/tcp
sudo firewall-cmd --add-port=55999/tcp
Note:
Use the same call with and without the --permanent option if you want to make a change in runtime and permanent configuration.
5. Create an Inbound Port Rule on every Azure host for given CLUSTER_PUBLIC_PORT parameter value, see example:
ADACLU-1
Network Security Group ... attached to Network Interface ...
Priority Name Port Protocol Source Destination Action
...
310 AllowAnyCustom56081Inbound 56081 Any Any Any Allow
...
65500 DenyAllInBound Any Any Any Any Deny
6. Start the database in the following order: DBID 81 on ADACLU-1, 82 on ADACLU-2, and 83 on ADACLU-3 (adastart <dbid>).
7. Add Adabas Client configuration settings for the cluster in the dbmapping file (see $ACLDIR/config/dbmapping.txt).
Adabas Client
# <cluster-id> = adatcp://<public-ip-1>:<public-port-1>?cluster=adatcp://<public-ip-2>:<public-port-2>; adatcp://<public-ip-3>:<public-port-3>
... e.g.
66 = adatcp://52.166.241.102:56081?cluster=adatcp://20.16.187.73:56082;adatcp://13.81.12.66:56083
8. Verify connection to cluster.
Adabas Client
[sag@ADABAS-CLIENT]$ getdbinfo 66
get platform and version info of database 66
Database 66 is active, V7.1.1.3, Platform = 21, opsys=UNIX/Windows, ADATCP access to '52.166.241.102:56081'
Sample Output
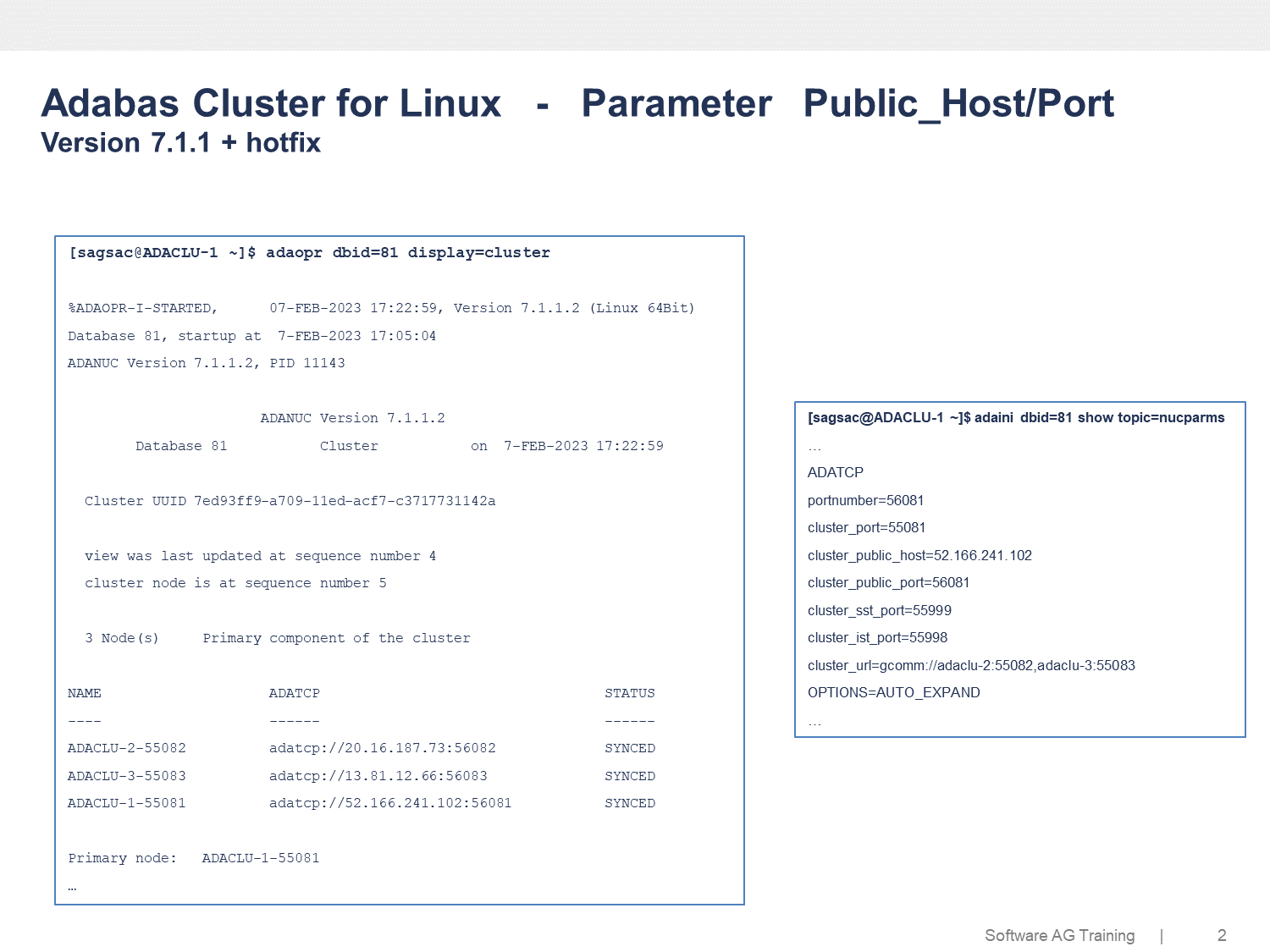
This graphic shows the ADAOPR utility output of DISPLAY=CLUSTER as well as the cluster related database INI entries of one node.